
As a result, a vast assortment of software engineers at Adobe and Google have scurried to shore up the vulnerabilities in Google’s Chrome browser, by far the most popular in terms of global market share. These changes, detailed in a blog post on Thursday, are said to have structurally modified the way Flash interacts with the operating systems installed on many PCs, thereby diminishing the likelihood of attacks.
Two major alterations have been added to Flash, one of which is not exclusive to Google Chrome and the other of which is exclusive, but will be added to other browsers come August.
The Chrome-only mitigation consists of a new partition added to the heap, a rather sizable collection of computer memory designed to isolate different objects from one another. As a result, one object in the memory pool cannot be exploited by hackers in order to meddle with others.
If heap partitioning had been included in Flash before the exploits were deployed, they would have been much more difficult to carry out. To be specific, the exploits performed by the attackers were accomplished by modifying the “Vector.” object after clearing some of the heap that it inhabited.
As a result, the attackers were able to infect computer memory, installing malware on the corresponding computer. A diagram below from Google Project Zero team members Mark Brand and Chris Evans illustrates how the breaches were executed.
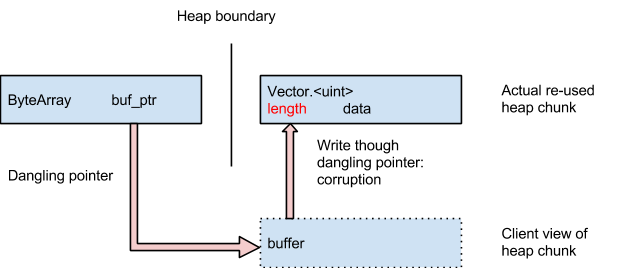
Thanks to the new design embedded below, a portion of unmapped space, referred to as “no man’s land,” is positioned between the Flash heap and System heap, making exploitation clearly more difficult.

To take full advantage of Google’s new security measure, make sure that you’re using the 64-bit version of Google Chrome if you’re on a 64-bit computer since the number of memory addresses in the 32-bit version pales in comparison. To check what version of Chrome you’re running, enter chrome://chrome in your address bar. Unless you see the string “64-bit” in the resulting window, you’re on the 32-bit version of Google Chrome and you may want to resolve this by switching to 64-bit to avoid security threats.
A second security effort, presented by Adobe, ensures that the attacker cites a validation secret prior to revising Vector objects. This preventive measure aims to protect users of 32-bit browsers and serves as a superlative demonstration of what researchers refer to as “defense in depth.” Adhering to this ideology, the Project Zero team is currently taking further action to ensure optimal protection against hackers. This includes browser sandboxes and compiler-based mitigations.
